Cryptography is the process of communicating securely in an insecure environment ie. More generally cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages3 various aspects in information security such as data confidentiality data integrity authentication and non repudiation4 are central to modern cryptography.
 How To Generate Your Very Own Bitcoin Private Key
How To Generate Your Very Own Bitcoin Private Key
Typical usage goes like this.

How does bitcoin public key cryptography work. Where other people can listen in and control the communication channel. The message you wish to send is converted to a cipher text that appears to be gibberish unless you know the secret to unlocking it. Each coin is associated with its current owners public ecdsa key.
Public key cryptography to the rescue. Public key cryptography is an essential part of bitcoins protocol and is used in several places to ensure the integrity of messages created in the protocol. Alice creates a publicprivate key pair.
The public key can be used to encrypt messages but not decrypt them. This is done through the use of public key cryptography. See my blog for more about bitcoin and its emerging opportunity trade crypto with the power of 100x leverage.
It can be publicly shared with anyone for example over t! he internet. How why it works. The genius of public key crypto! graphy is that it utilises two encryption keys.
Basically public key cryptography means that you have a publicprivate pair of keys. Wallet creation and signing of transactions which are the core components of any currency rely heavily on public key cryptography. They do this in such a way that only the sender can put this signature on the message but anybody in the network can verify that it was the sender who signed the message.
Traditional blockchain implementations such as those of bitcoin and ethereum use public key cryptography often referred to as asymmetric cryptography in several aspects of their protocols. The first key known as the public key is used to encrypt information. When you send some bitcoins to someone you create a message transaction attaching the new owners public key to this amount of coins and sign it with your private key.
The private key is as the name suggests secret and can be used! to decrypt the messages. How does cryptography work. The other key feature in the bitcoin system is the transaction block chain.
Rsa public key encryption algorithm cryptography. This broadcast is public knowledge and open to everyone. This is basically a public ledger which has the record of every transaction since the very beginning of bitcoin.
First is public key cryptography. Think about receiving radio signals on your cars radio that allows you to listen to the broadcast.
 Public Key Cryptography
Public Key Cryptography
 How To Setup Bitcoin Cold Storage Get Started Bitcoin Com
How To Setup Bitcoin Cold Storage Get Started Bitcoin Com
 The Bank Of England Is Planning A Bitcoin Style Virtual Currency
The Bank Of England Is Planning A Bitcoin Style Virtual Currency

 The Wonderful World Of Elliptic Curve Cryptography Coinmonks Medium
The Wonderful World Of Elliptic Curve Cryptography Coinmonks Medium
Bitcoin Transaction
 Learn All A! bout Cryptocurrencies Cryptography Because It Works
Learn All A! bout Cryptocurrencies Cryptography Because It Works
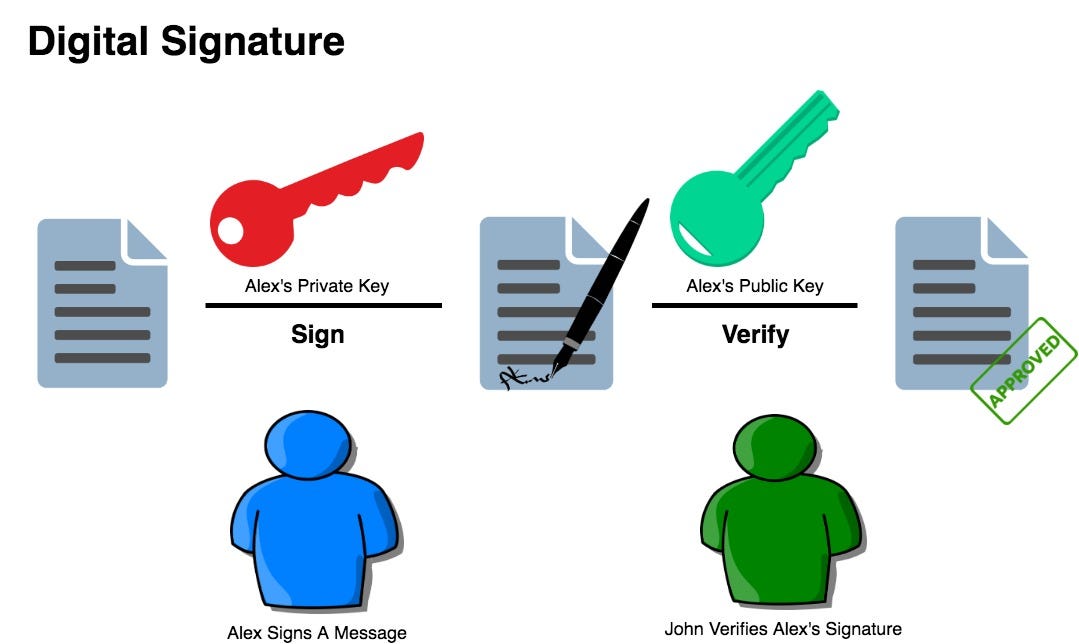 Blockchain Public Private Key Cryptography In A Nutshell
Blockchain Public Private Key Cryptography In A Nutshell
Bitcoin Digital Signatures Video Khan Academy
Bitcoins The Hard Way Using The Raw ! Bitcoin Protocol
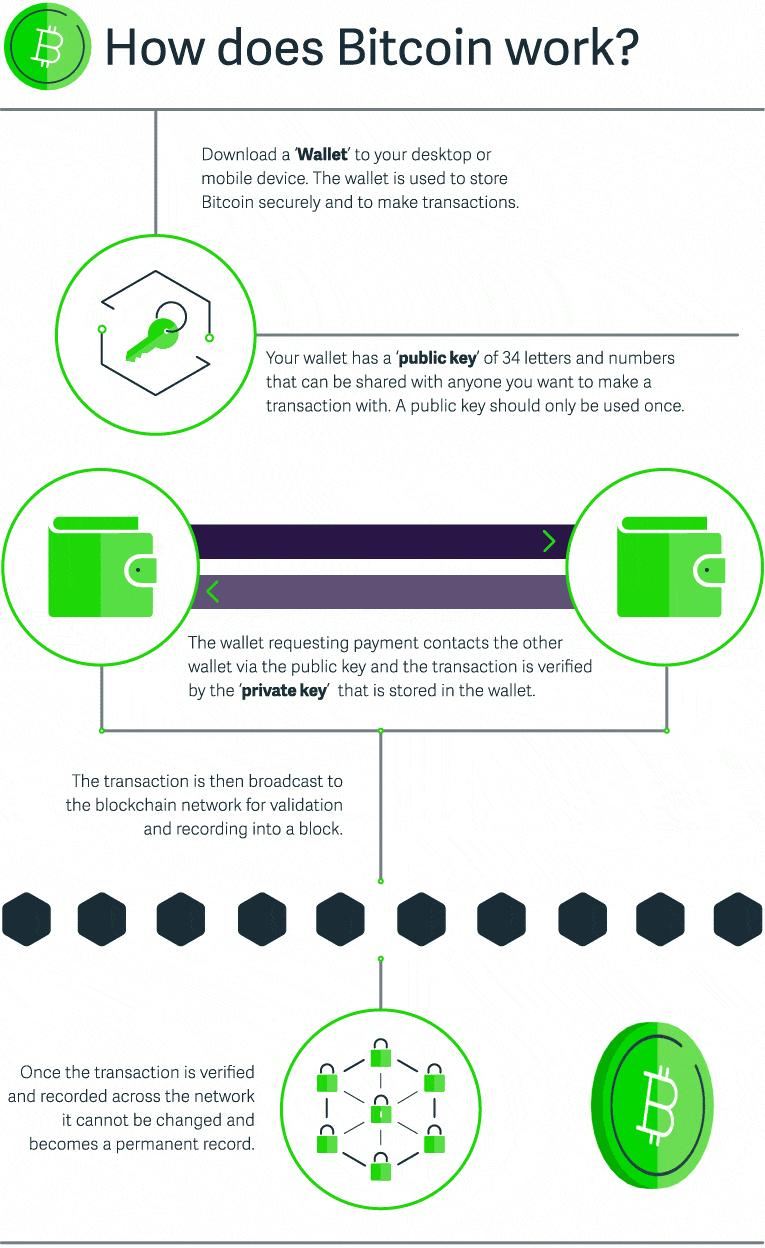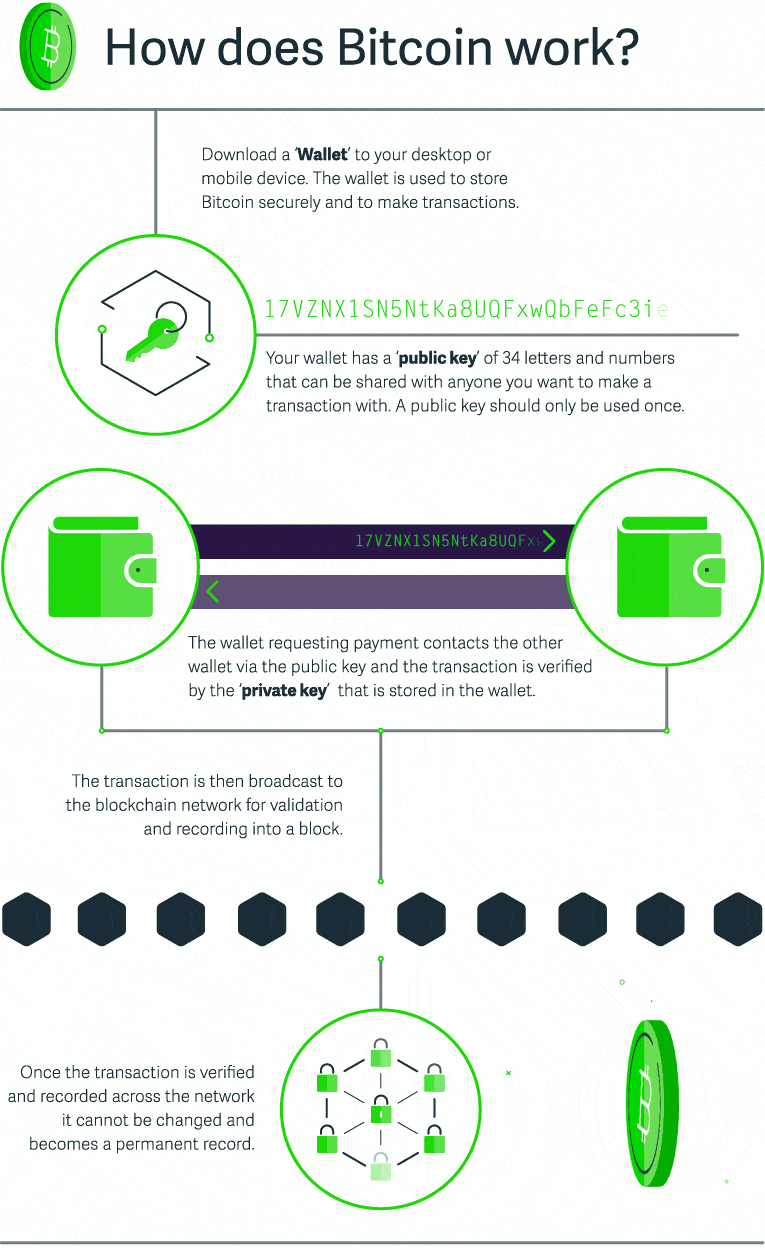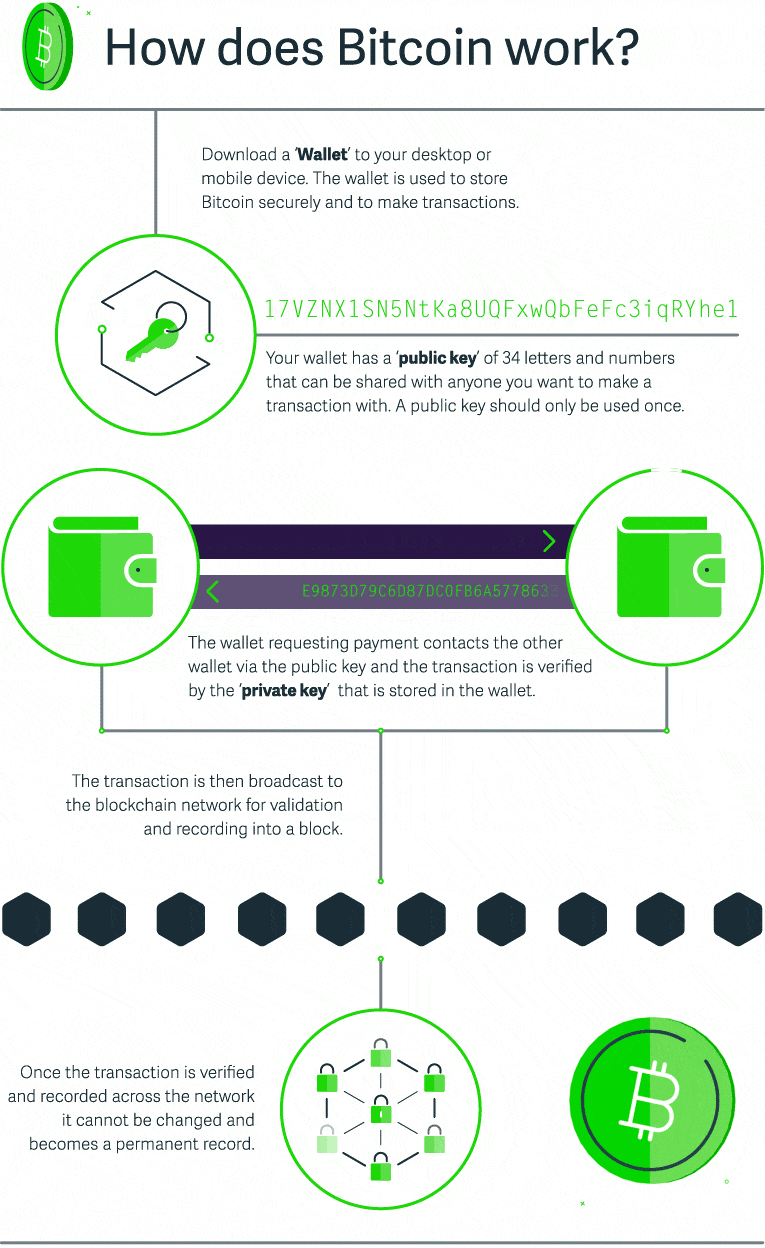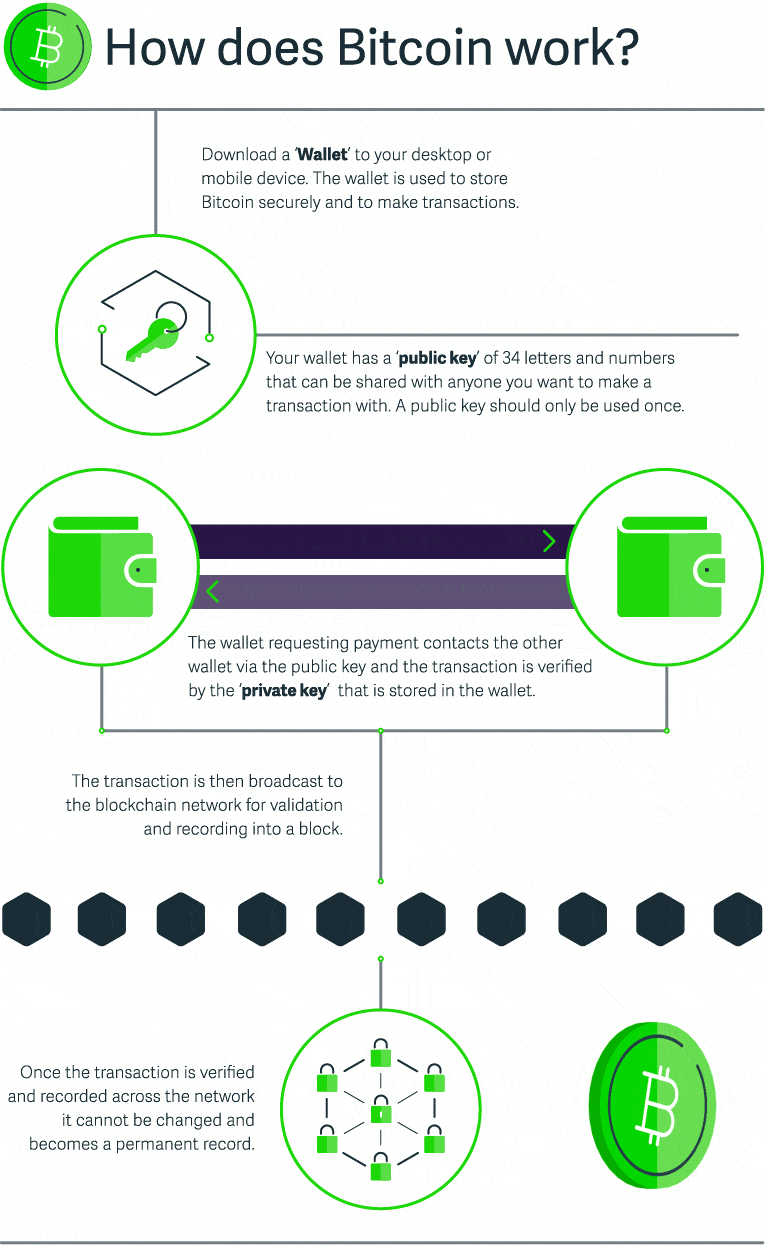 Blockchain Cryptocurrency And Bitcoin For Businesses Sage Advice
Blockchain Cryptocurrency And Bitcoin For Businesses Sage Advice
 Public Key Cryptography What Is It Video Khan Academy
Public Key Cryptography What Is It Video Khan Academy
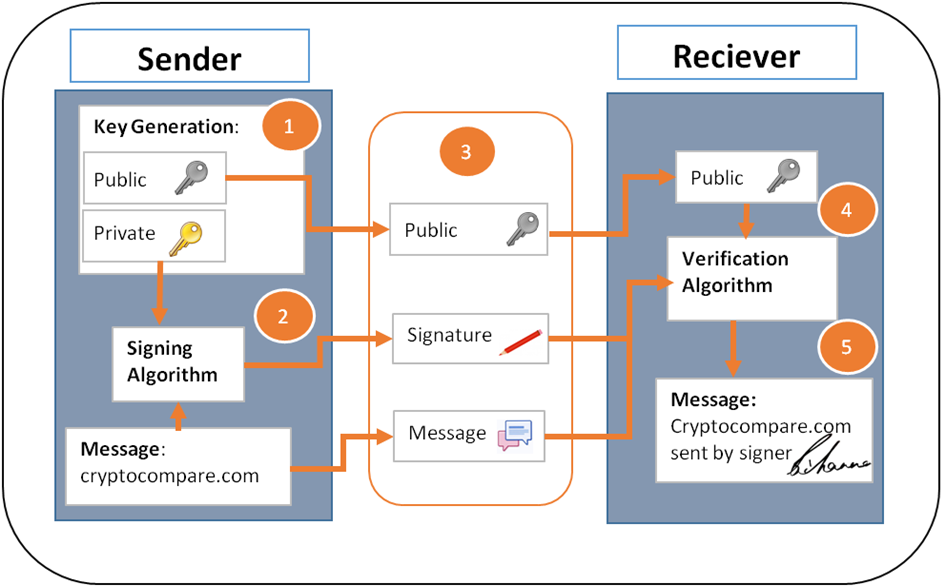 How Does Bitcoin Cryptography Work Cryptocompare Com
How Does Bitcoin Cryptography Work Cryptocompare Com
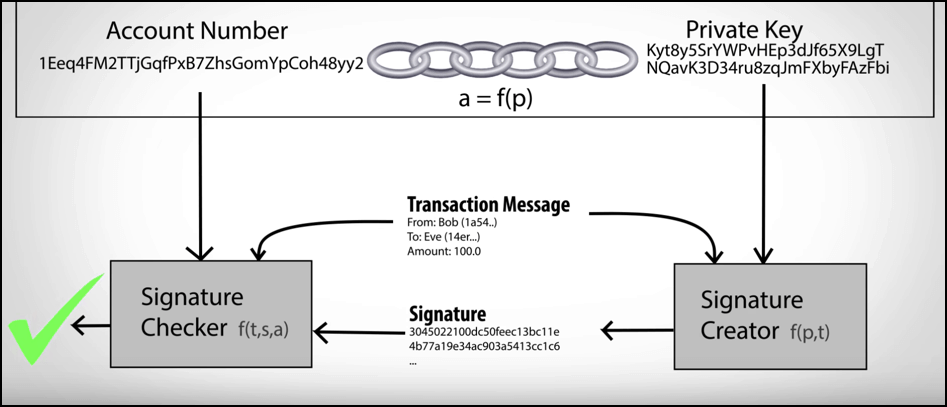 Bitcoin Private Key Noob To Expert Guide
Bitcoin Private Key Noob To Expert Guide
 Blockchain Tutorial 11 Elliptic Curve Key Pair Generation
Blockchain Tutorial 11 Elliptic Curve Key Pair Generation
